You’ve heard about the DNS while configuring your internet connection. You enter two DNS values, one primary DNS and another secondary DNS. DNS is fundamental for the functioning of internet. Through this article, I will explain what DNS is, why it is necessary, how it works and a simple DNS cache poisoning attack. Let’s get started…
What is DNS?
DNS stands
for ‘Domain Name System’. The official Wikipedia definition goes something like
this:
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network.
The Domain Name System (DNS) is a hierarchical distributed naming system for computers, services, or any resource connected to the Internet or a private network.
Basically,
DNS is a service that translates human recognizable domain names (such as www.google.com,
twitter.com etc) to their respective IP addresses.
On the
internet or any IP network, computers and servers recognize each other by their
IP address and not their domain names like google.com. Therefore, it is
necessary to convert the domain name which you type in the address bar of your
browser to its respective IP address i.e. the IP address where the server
residing. Then your browser can establish connection with that server and start
exchange of data.
Why DNS is necessary?
It’s
difficult for ordinary people to remember hundreds of IP addresses which belong
to different web servers. Naturally it’s easier to remember the domain names.
This practice of using simpler names, rather than IP addresses, dates back to
the ARPANET era. Computers used to have something called as a ‘hosts’ file
which mapped computer names to their respective ip address.
In 1983 the
DNS was invented which was followed by BIND server, the first DNS server based
on unix platform. This eliminated the need for end users to maintain a hosts
file.
Another
advantage of DNS is that, even if the web server changes its IP address or
migrates from one location to the other on internet; its domain name remains
the same. Hence end user does not need to worry about the mapped ip address by
the DNS service. The DNS servers can add or update DNS entries/records
internally.
How does DNS work?
From a
client’s point of view, working of DNS is very simple. It sends the request to
the configured DNS server. The server sends back the answer and the client
establishes a connection with that host. The sequence of steps that take place
are as follows:
1. User types www.example.com in his web
browser.
2. The computer sends request to the DNS
server that it is configured to use. The request goes like this – “Where is www.example.com?”
3. The DNS server receives this request
and begins looking up its database to find entry for www.example.com. Luckily, this time, it finds
the entry and corresponding IP address (say 192.0.43.10).
4. It replies back to the client – “www.example.com
is at 192.0.43.10”
5. Client receives this response and
starts communicating with the ip address.
Actually, DNS is a distributed system. All the DNS servers
are interdependent to resolve an IP address completely. Suppose you made a DNS
query for www.microsoft.com and the DNS server you are assigned to, finds that
it doesn’t have that record present in its database. How can it find out where www.microsoft.com
resides?
Structure of the
distributed system
To find out where a particular host belongs, the client has
to make recursive DNS queries to reach to the authoritative name server for
that particular domain. As the name implies, authoritative name servers have authority
over their respective domain name. Authoritative name servers can assign
authoritative name servers for their sub domains. Anyway, look at the following
hierarchy of the distributed domain name space. Yup, it’s a tree as we studied
in the discrete mathematics class… :-P
Whenever a client has to find an IP address corresponding to
a host, say, www.microsoft.com, it performs recursive DNS queries on the
respective authoritative name servers. A root name server has authentic records
of all the ‘Top level domains’ (.com, .org, .net etc.). The name servers for
TLDs have records for all the domain names under them e.g. example.com,
google.com etc. The process goes like this…
Client : I wanna go to www.microsoft.com, but I don’t have any
records corresponding to that. I know, I’ll ask the root name server.
*client sends request to root name server*
Root name server : Hmm, I see you’re going to a “.com”
domain, Here’s the address of “.com” TLD. Go and ask him.
*client receives the address sends
request to .com TLD server*
.com TLD : Well, Microsoft.com comes under me. And here’s
the address of “Microsoft.com” authoritative name server. You’ll get your
answer from there!
*client receives the address and
sends request to Microsoft.com nameserver*
Microsoft.com NS :Hello, You’ve come to right place. I’m
the authoritative nameserver for www.microsoft.com and here’s its IP address.
*client receives the address of www.microsoft.com
and starts communication with the web server*
Poof, as you can see, resolving domain names is a complicated
process and generate a lot of load on the root nameservers as well as TLD
nameservers.
To overcome this, your local DNS servers (maybe servers
assigned by your ISP) cache the DNS records in their own database such that
each time a client makes a request, they don’t have to make recursive DNS
queries. They can respond with the matching DNS record entry in their own
cache. This also takes away a lot of load from root and TLD nameservers.
DNS Cache Poisoning:
Alright, now let’s look at DNS from a hacker’s point of view.
If one can manipulate the records in the DNS cache server, the records are said
to be poisoned. An attacker can change the IP address corresponding to a
legitimate domain name. Whenever a client requests for this legitimate domain
name resolution, they’ll be provided with this spoofed IP address which the
attacker inserted. The attacker may have hosted some malicious website on this
ip address or maybe created a replica of the original legitimate website for
phishing purposes. The number of things an attacker can do with a spoofed DNS
record are many. In a nutshell, a poisoned or a compromised DNS server provides
invalid or illegitimate DNS resolutions which may point to malicious websites.
Local DNS cache poisoning:
As we’ve seen before, each computer has a ‘hosts’ file which
maps domain names to their corresponding IP addresses. Remember when I said
client goes to its local DNS server when the user types in a website name? I
lied. :-P First of all, the client checks its own ‘hosts’ file if it can find
the corresponding entry there. If it doesn’t, then it goes to the local DNS
server. Here we’re going to manipulate the hosts file on our PC to redirect
some legitimate website names to wherever we want.
Windows users can find the hosts file at the following
location:
C:\Windows\System32\drivers\etc\hosts
Remember
that hosts file does not have any extension.
Linux
users, the hosts file is located at:
/etc/hosts
Edit
the hosts file with your favorite editor. Remember that you need administrator
privileges on windows and root privileges on linux to be able to do that.
Anyway,
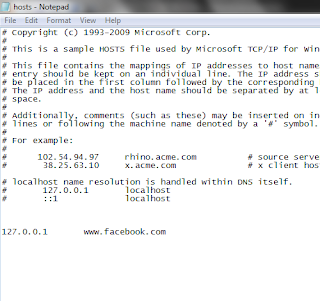
the hosts file may look like this:
Now
add the following text to the end of the file:
127.0.0.1 www.facebook.com
On
windows, it will look like this:
Here,
www.facebook.com is the website name which will get redirected, you can replace
this with any other website name you want. 127.0.0.1 is the IP address where www.facebook.com
will point to. In our case, this is the local loopback IP address, you can
replace this by any other ip.
Save
the file and try opening www.facebook.com or whatever website name you typed
through your browser. It will open your localhost and if there’s no web server
currently running, it will say page cannot be displayed.
There
are some applications of manipulating hosts file. In home or office
environment, a hosts file can be used to block social networking and adult
pornography websites just by setting them to point to your localhost or any
other webpage on your network containing a warning. Also hosts file can be used
for DNS cache poisoning as we saw just now. Legitimate website names may
redirect you to a malicious website which may try to introduce Trojans, viruses
on your PC or try to phish your online banking or social networking account.
One
may also write a simple bash script or a batch file that may manipulate or
replace hosts file automatically. This technique is been used in some viruses
and worms to poison DNS cache of thousands of innocent users to land them on
malicious or spoofed websites. It is advisable to follow the best security
practices.
Thank
you for following me throughout this article and I hope you’ve found this
informative. Waiting for your comments… :)
This
article is for information purposes only.


No comments:
Post a Comment